As the challenge of securing a rapidly expanding array of IoT devices grows, understanding IoT security architecture becomes essential for safeguarding the technology that has reshaped our world. IoT connects everything from wearables and home appliances to industrial machines and smart city infrastructure. However, as the number of IoT devices increases, so does the potential attack surface, making security an ever-present concern. In this blog, we will explore IoT security architecture in depth, focusing on developers' unique challenges in securing diverse and complex IoT ecosystems.
What is IoT security architecture?
In simple terms, IoT security architecture refers to the layered framework designed to protect IoT devices, networks, and data from cyberattacks. Because IoT ecosystems involve various interconnected components, from physical sensors to cloud services, it’s crucial to ensure that security measures are embedded across every layer.
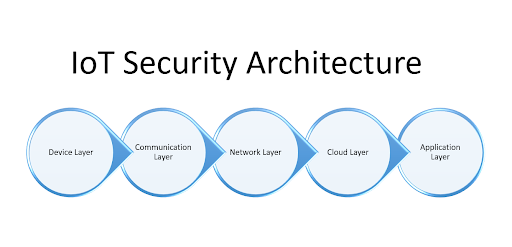
Key components of IoT security architecture
1.Device layer: The hardware (sensors, actuators, etc.) and firmware running on the IoT devices are highly vulnerable. Ensuring secure boot processes, secure storage, and integrity checks is critical at this layer.
2.Communication layer: Devices communicate using protocols like MQTT, CoAP, HTTP, or proprietary systems. Ensuring encryption (TLS/SSL) and data integrity is vital to prevent man-in-the-middle attacks.
3.Network layer: The network requires protection against attacks like Denial-of-Service (DoS), eavesdropping, and data tampering. Techniques such as firewalls, intrusion detection systems, and network segmentation can help.
4.Cloud layer: IoT devices often interface with cloud platforms to store data or process complex computations. Ensuring the cloud's security with mechanisms like API authentication, access control, and secure data storage is essential.
5.Application layer: User-facing applications need security from the interface to the backend. Strong identity management, regular security updates, and secure data processing practices are essential considerations at this layer.
Unique IoT security challenges
IoT security brings unique challenges compared to traditional IT security because of the heterogeneous nature of IoT devices, the complexity of their communication patterns, and the sheer scale of deployments. Let’s explore some of the key challenges that make securing IoT ecosystems tricky.
1. Resource constraints IoT devices are often designed with efficiency in mind. They have small batteries, limited processing power, and minimal memory, as they're meant to function in resource-tight environments like sensors in smart homes or wearable tech. But this minimalism creates a security headache. Security features like encryption and real-time threat detection require more processing power and memory, which can drain resources and slow the devices down. Balancing performance and security is challenging. While encryption is crucial, resource-intensive algorithms like AES and RSA can strain devices. Developers are turning to lightweight alternatives like Elliptic Curve Cryptography (ECC), which offers similar protection with less computational load.
2. Diverse IoT devices IoT encompasses many devices from smart thermostats to industrial sensors, each with unique hardware and protocols. Creating a one-size-fits-all security solution is challenging. Standards like Lightweight M2M (LwM2M) can help, but adaptable security solutions remain essential.
3. Weak authentication mechanisms Many IoT devices have weak default security settings, making them easy attack targets. Implementing mutual authentication, certificate-based security (e.g., Trusted Platform Modules), and multi-factor authentication (MFA) can help improve device protection.
4. Data privacy and integrity IoT devices handle sensitive data; breaches can lead to privacy violations or control system tampering. Encrypting data at rest and in transit, along with methods like anonymization and homomorphic encryption, can safeguard information while allowing secure data processing.
5. Firmware vulnerabilities and lack of updates Firmware on IoT devices often has vulnerabilities, and updates are infrequent. Over-the-air (OTA) updates, ideally encrypted and digitally signed, can secure devices more effectively by simplifying user-friendly, secure updates.
6. Scalability of security solutions Securing millions of devices across networks requires scalable security solutions. Automated security processes, like real-time monitoring and updates via cloud-based platforms, enhance threat response and reduce administrative burden.
7. Physical security Remote IoT devices, like public cameras or industrial sensors, are vulnerable to physical attacks. Tamper-resistant hardware, intrusion detection, and secure enclosures can help protect devices in sensitive or inaccessible areas.
Integrating the Purdue Model into IoT security architecture
To tackle the unique challenges of IoT security, we can implement a standard model or framework. One of the most recognized frameworks is the Purdue Model, also known as the Purdue Enterprise Reference Architecture. This model is designed to improve cybersecurity in industrial control systems (ICS), such as those found in factories and power plants. It structures ICS into distinct layers, each assigned specific tasks and security responsibilities. Imagine an industrial setup with distinct layers, from business operations to machinery control. The Purdue Model defines these levels and assigns security needs, creating zones that limit risk and prevent threats from spreading across the system. A key benefit is network segmentation, which reduces the “attack surface” by separating business functions from machine control. It also helps monitor access, control data flow, and respond quickly to issues. The Purdue Model offers a strong theoretical foundation for industrial system security, but it falls short in addressing the practical challenges of today’s highly connected IoT environments. Originally developed for isolated ICS setups, the model lacks the flexibility to secure modern systems that involve real-time data exchanges, remote access, and IT-OT convergence. To fully protect IoT-integrated architectures, organizations need practical, adaptive solutions that go beyond theory, tailored to the unique demands of today’s industrial setups. In the next section, we will see how to translate the Purdue Model’s framework into actionable, resilient defenses for evolving IoT security needs.
Practical solutions for addressing IoT security architecture challenges
Given the unique challenges IoT presents, we need to adopt tailored security strategies. Let's see some real-world solutions that can be implemented to ensure better security in IoT devices.
1. Adopt a Zero-Trust architecture:
In traditional networks, devices inside the network were automatically trusted. However, with the rise of the Internet of Things (IoT), it’s risky to assume that any device is secure. The Zero-Trust Model changes this approach by ensuring that no device is trusted by default, even if it’s already within the network.
Example: Smart home security camera
Consider a security camera in your smart home setup. In a traditional model, this camera would assume the home network is safe. In a Zero-Trust architecture, the camera must regularly prove it’s not compromised through cryptographic checks before transmitting video footage.
Key methods for implementing Zero-Trust architecture:
- One crucial aspect of Zero-Trust is continuous authentication. This means that devices must re-authenticate at every step. For example, when a smart thermostat connects to the home Wi-Fi, it must verify its identity at regular intervals, not just once during installation.
- Another important element is device identity. Each device’s identity is secured using cryptographic keys and hardware roots of trust. Think of these as "digital fingerprints" for devices, ensuring that even if someone intercepts the data, they cannot pose as the device.
2. Use network segmentation
Not every device needs to communicate with every other device. By grouping IoT devices based on their function or risk level, you can prevent an infected device from taking down your entire smart home.
Example: Smart fridge hack
Imagine if your smart fridge gets hacked. If it’s in its micro-segment, it cannot interact with your smart thermostat or home security system. This isolation keeps your house safer overall.
Methods for implementing network segmentation:
- One effective way to enhance security is through micro-segmentation. This involves creating virtual mini-networks (or VLANs) for groups of IoT devices. For instance, your smart lights might be on one segment, while your security cameras are on another.
- Another approach is risk-based isolation. High-risk devices, such as third-party IoT gadgets purchased online, should be isolated from mission-critical systems like home security to minimize potential vulnerabilities
3. Implement encryption at every layer:
Encrypting data means scrambling it to make it useless to anyone without the right decryption key. In the context of IoT, encryption needs to occur at multiple points: both when data is stored (at rest) and when it moves between devices or servers (in transit).
Example: Smart doorbell security
Consider your smart doorbell that stores video clips. Even if a hacker physically steals the device, the encrypted data ensures they cannot access the recordings without the proper decryption key.
Best practices for encryption:
- To secure communications between devices and servers, use TLS 1.2+. For instance, when your fitness tracker uploads your steps to the cloud, TLS encrypts this transfer, protecting your data during transit.
- Additionally, if your IoT camera records footage, ensure that the stored video on the device’s internal storage is encrypted. This way, if the camera is stolen, the footage remains protected.
4. Device health monitoring:
IoT devices can become outdated or vulnerable over time. Regularly checking their "health" ensures they are running the latest security patches, preventing them from becoming easy targets.
Example: Smart lock security
Consider your smart lock that hasn’t been updated in a while. If a new vulnerability is discovered, you might remain unaware without a health check system. However, with automated monitoring, the system can push the latest security patch, ensuring your smart lock remains secure.
Best practices for device maintenance:
- Ensure your IoT devices have a built-in update agent that automatically pushes updates. This helps keep devices secure without requiring manual intervention.
- You can create dashboards that allow users to monitor the status of all their IoT devices, including aspects of IoT security architecture. For instance, users can check if firmware is up to date or if any device has been flagged for a vulnerability.
5. Use access control models:
Not everyone or every device needs access to every feature within the IoT ecosystem. By restricting access, you can minimize potential damage if something goes wrong.
Example: Home network access
You might set up your home network so that only you can access the security cameras, while everyone in the house can adjust the thermostat. This way, even if your child's tablet gets compromised, your cameras remain off-limits to potential hackers.
Access control models:
- Role-Based Access Control (RBAC): Assign roles to users and devices, limiting their permissions. For instance, your kids might control the smart lights, but they won’t have access to the security cameras.
- Attribute-Based Access Control (ABAC): Control access based on attributes such as device type, location, or time of day. For example, your smart garage door might only respond to your phone during specific hours.
By applying these practical strategies, you can build more secure IoT systems and help prevent some of the major security risks that arise from the growing number of connected devices. The key is to always anticipate risks and apply layers of defenses, kind of like building a digital fortress for your smart world.
Best practices for securing IoT
In addition to implementing practical strategies, it's essential to embrace best practices when developing IoT systems. Let’s see some of these best practices below:
Adopt a layered security approach: Secure each layer of the IoT architecture (device, communication, network, cloud, and application) independently, using defense-in-depth strategies.
Implement secure boot: Ensure that devices boot with only trusted and signed firmware, and verify the integrity of firmware updates.
Encrypt data: Use encryption (e.g., TLS/SSL) to secure data in transit, and encrypt sensitive data at rest, whether stored on the device or in the cloud.
Use strong authentication: Implement strong authentication mechanisms for both devices and users, avoiding hard-coded passwords or weak credentials.
Regular updates and patching: Ensure that devices can receive regular, secure, and signed firmware updates, and encourage users to apply them promptly.
Monitor and respond to threats: Incorporate intrusion detection systems, logging, and real-time security monitoring to detect and respond to potential threats quickly.
Device lifecycle management: Consider security from the device’s initial deployment to decommissioning, ensuring that sensitive data is wiped, and certificates are revoked when devices are retired.
Conclusion
IoT security architecture is complex, mainly due to the diverse nature of IoT ecosystems and the unique constraints of devices. As developers, it’s crucial to embrace a holistic approach to security that involves multiple layers of protection, strong cryptography, and robust authentication practices. Despite the unique challenges, by adhering to best practices and keeping security at the forefront, we can build resilient and secure IoT solutions that protect both users and organizations from emerging threats.

